Which Statement Describes the Best Practice for Securing a Load
Port security cannot be enabled on a trunk and trunks are the only types of ports that have a native VLAN. The load history for Snowpipe operations is stored in the metadata of the pipe object.
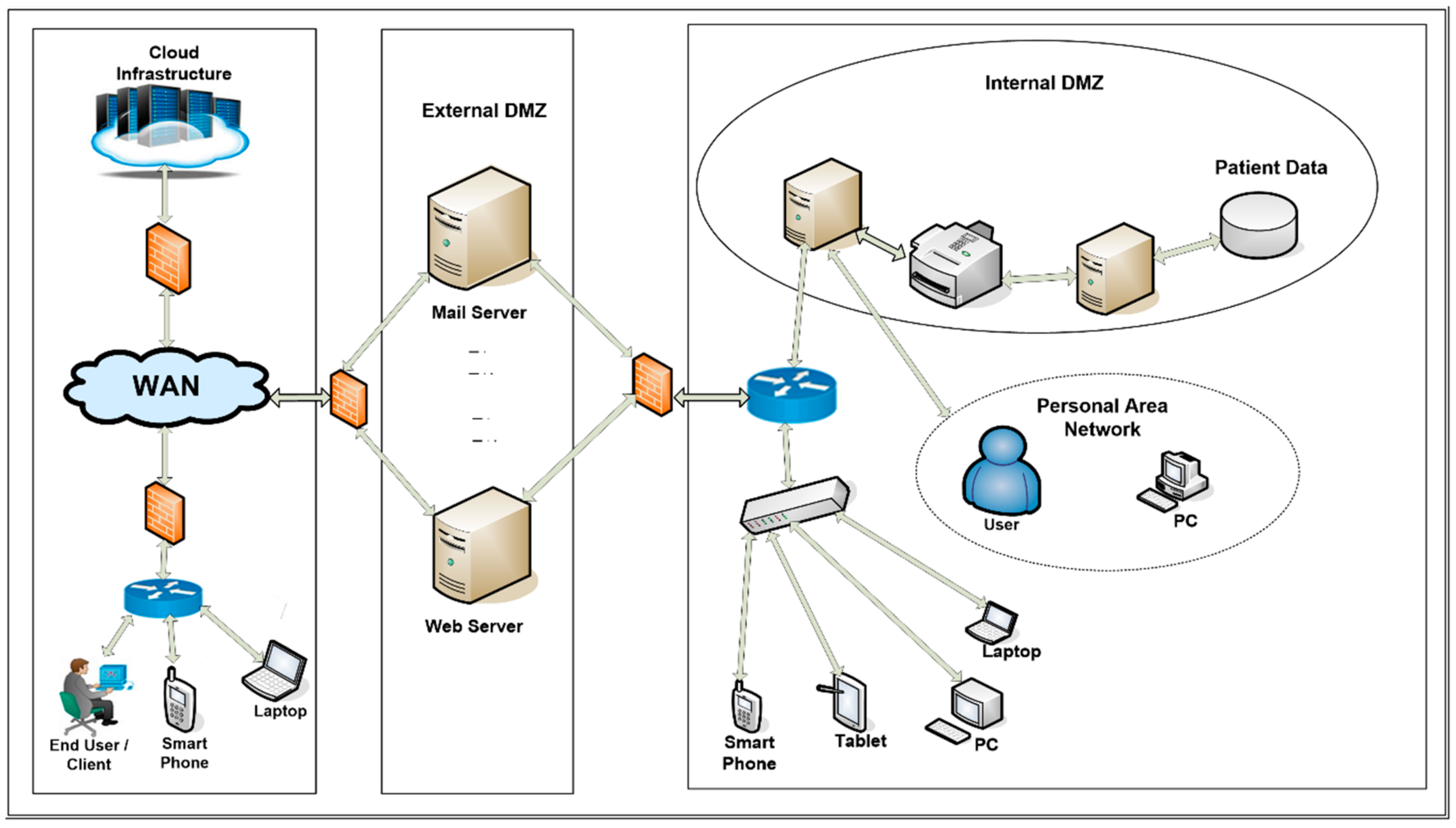
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
Even though turning DTP off on a trunk is a best practice it does not have anything to do with native VLAN risks.

. If both of these were in an ACL the SNMP ACE is more specific than the UDP statement that permits a range of 10001 UDP port numbers. Consider the two permit UDP statements. Examine the following options and determine which describes the infection type.
These best practices will address the constraints placed on the ETL system and how best to. This document describes the best practice and alternative scenario for deploying ASA-5500 VPN remote access solution in a Load BalancingClustering environment using digital certificates authentication. Reduce local Administrators group membership on all AD FS servers.
Citizenship and Immigration Services Form I-9 and providing supporting documentation. Best practices are recommendations that can help you use AWS CloudFormation more effectively and securely throughout its entire workflow. Configure the SQL server for initial data load.
Deploying an application across multiple availability zones. Get answers to platform specific questions from Anaplanners everywhere. When you plan to initially load a lot of data you can shorten the time it takes to populate the database by temporarily turning off full-text search and turning it on again after the export on the MIM 2016 management agent FIM MA has.
The purpose is to determine tax identification and withholding. A users PC is infected with a virus that appears to be a memory resident and loads anytime an external universal serial bus USB thumb drive is attached. Workshop content submit for approval and contribute best practices to the Community.
Which connections use a virtual private gateway in an Amazon VPC. Load securing also known as cargo securing is the securing of cargo for transportation. Name Extract Transform Load ETL Best Practices Description In defining the best practices for an ETL System this document will present the requirements that should be addressed in order to develop and maintain an ETL System.
Complete your training with support from the experts. Learn how to plan and organize your stacks create templates that describe your resources and the software applications that run on them and manage your stacks and their resources. AWS Certified Cloud Practitioner 6 full practice tests Set 2.
Which of the following examples supports the cloud design principle of design for failure and nothing will fail. Written to the partition table of a disk. In general this condition only affects users if they subsequently execute an ALTER PIPEREFRESH statement on the pipe.
The following is a list of best practices and recommendations for hardening and securing your AD FS deployment. Cargo that is improperly secured can cause severe accidents and lead to the loss of cargo lives and. When a pipe is recreated the load history is dropped.
To prevent security breaches that take advantage of the native VLAN place the native VLAN in an unused VLAN other than VLAN 1. Which type of load balancer would most benefit websites and mobile applications that run containers on Amazon Elastic Compute Cloud Amazon EC2 instances. Distributes load to a single server.
Which of the following statements best describes the purpose of completing Department of Homeland SecurityUS. For more information on VPN Load BalancingClustering High Availability services of the ASA appl. An input device sends information to the computer and an output device sends information to the computer.
Doing so could load duplicate data from staged files in the storage location for the pipe if the data was. A best practice for configuring an extended ACL is to ensure that the most specific ACE is placed higher in the ACL. Deploying multiple EBS volumes for EC2 Instances.
Hardware virtual private network VPN AWS Direct Connect DX Which statement describes the purpose of simple routing with Amazon Route S3. There are many different ways to implement a load balancer. This helps to distribute the load over multiple machines and depending on the load balancing option can automatically reroute connections if a TiDB instance becomes unavailable.
Require all cloud admins use Multi-Factor Authentication MFA. IT Essentials Version 700 - IT Essentials 70 Chapter 10 exam Answers full new questions v701 v60 100 scored 2021 2022 pdf file free download. Uses a local scripting engine.
A best practice is to use custom route tables for each subnet which enables granular routing for destinations. Ensure only Active Directory Admins and AD FS Admins have admin rights to the AD FS system. Reducing the costs for your solution.
SecDevOps sometimes called Rugged DevOps or security at speed as a set of best practices designed to help organizations implant secure coding deep in the heart of their DevOps development and deployment processesIt seeks to embed security inside the development process as deeply as DevOps has done with operations. Which statement describes what the AWS Support Concierge service provides. Which of the following statements is true.
The purpose is to establish identity and employment authorization. Share ideas for platform improvements training the Community and more. According to the European Commission Transportation Department it has been estimated that up to 25 of accidents involving trucks can be attributable to inadequate cargo securing.
An input device sends information to the computer and an output device receives information from the computer. Elastic Load Balancing is managed by AWS and scales automatically. This section describes the most common types.
The SNMP ACE would be entered before the other UDP ACE. The initial load of data can be a lengthy process.

What Is Application Security Vmware Glossary

The Three States Of Data Guide Description And How To Secure Them
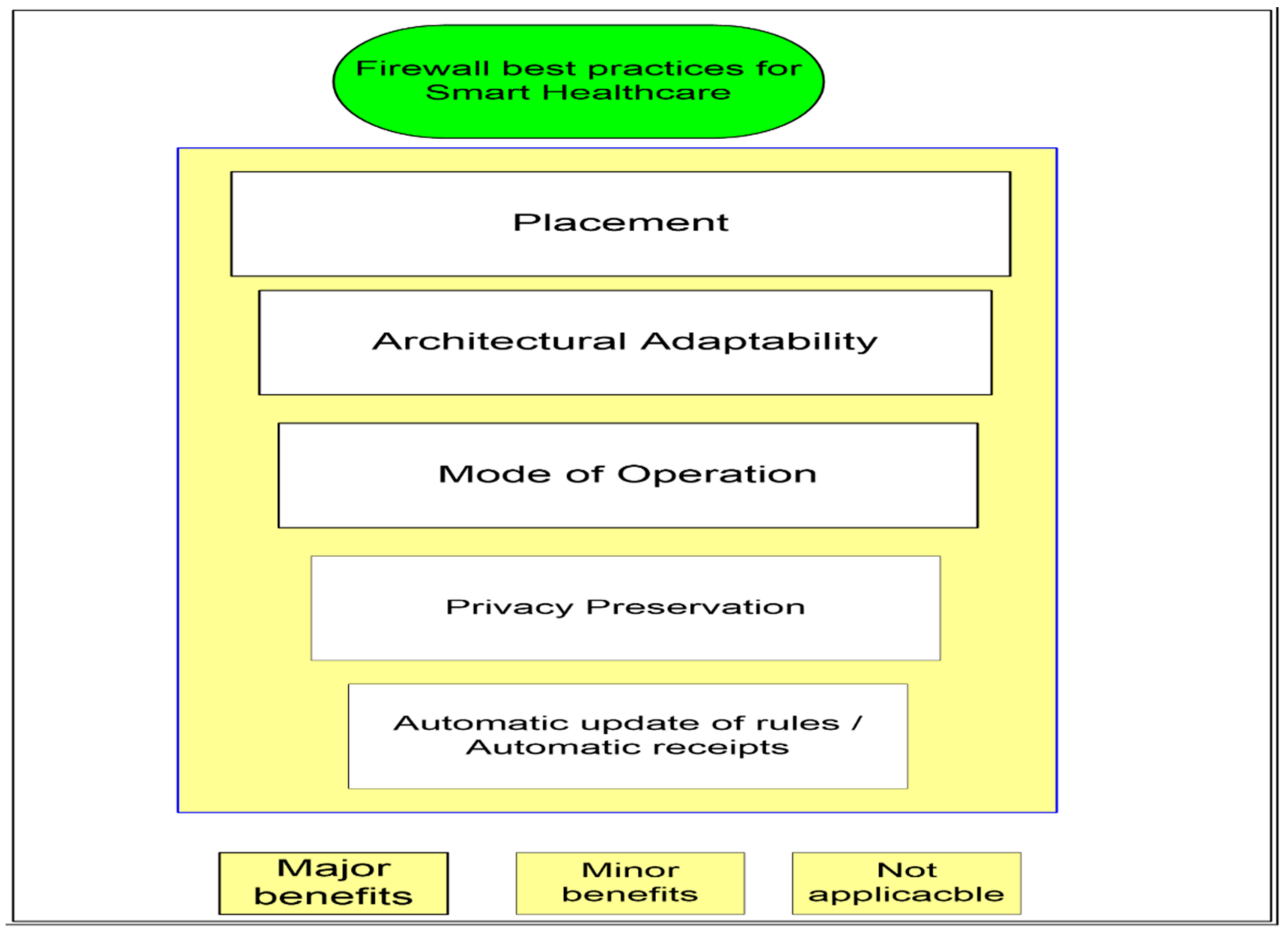
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
0 Response to "Which Statement Describes the Best Practice for Securing a Load"
Post a Comment